Unlocking Encryption for Consumer-Grade Applications, How Can zkTLS Enable On-Chain "Visa"?
Original Title: zkTLS: Unlocking Crypto Consumer Apps
Original Author: @yeak__, @Delphi_Digital Researcher
Original Translation: zhouzhou, BlockBeats
Editor's Note: TLSNotary verifies communication between the client and server, allowing selective data disclosure while ensuring privacy. Pluto introduces TLSNotary to smart contracts, Primus Labs enhances efficiency and develops zkFHE scheme, Opacity prevents collusion through Eigenlayer AVS and TEE, enhancing security. Opacity requires Web2 account verification, reducing Sybil attack risk, and adopts a verifiable log mechanism. Future optimization directions include vector blinding linear assessment to improve MPC efficiency for faster TLS proofs. HTTPS proxies act as intermediaries to enhance security and privacy protection, commonly used for enterprise traffic monitoring.
The following is the original content (slightly rephrased for better readability):
The encryption industry has always possessed a mindset, talent, and funding to change the world, but often lacks the means to achieve this goal. Currently, most real-world encryption success cases still rely on the support of Web2 giants. We can only hope that Visa and Mastercard continue to support crypto cards, Coinbase, PayPal, and Stripe keep optimizing the compatibility between traditional payment systems and blockchain, BlackRock continues to promote tokenization of government bonds, and Walmart keeps selling Pudgy Penguins.
Today, we have a powerful new tool that allows encryption industry builders to truly drive change. The traditional markets are rife with inefficiencies and limitations, while the encryption industry is in an unprecedentedly advantageous position to offer alternative solutions.
zkTLS (also known as TLS Oracle or Web Proof) enables private data to be extracted from the Web2 closed ecosystem, allowing users to prove various data types such as legal identity, financial records, educational background, and behavioral patterns in a completely privacy-preserving manner. Here is a brief overview of how it works.
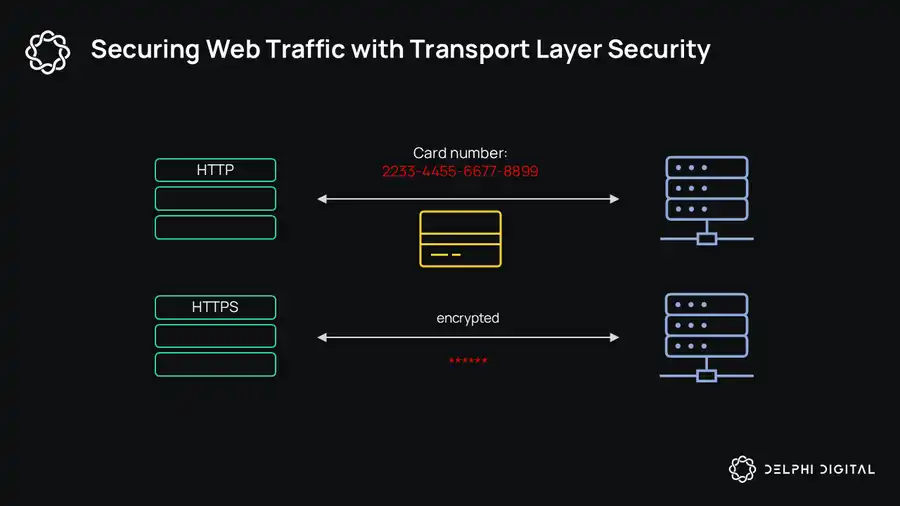
TLS (Transport Layer Security protocol) is a protocol used to encrypt communication between clients and servers. TLS makes up the "S" in HTTPS (HTTPS = HTTP + TLS) and has become a network standard, protecting 95% of network traffic.
TLS is a trusted centralized authority responsible for issuing session keys. When a user accesses a website, the browser and the target server perform a TLS handshake to generate a session key for subsequent data transmission using symmetric encryption. However, the data exchanged between the client and server is not signed, making it impossible to prove its authenticity elsewhere.
Security provided by TLS:
· Authenticity
· Integrity
· Privacy
· Lack of data portability
zkTLS accomplishes identity verification between the client and server during an HTTPS session and brings privacy-preserving proofs onto the chain, addressing the issue of data portability. Importantly, this is often undetectable by the server and cannot be blocked by a firewall. With zkTLS, the entire Internet's database can become a composable building block for blockchain applications, a task that Web2 is almost powerless to achieve.
Various implementations of zkTLS: MPC (Multi-Party Computation), Proxy, TEE (Trusted Execution Environment)
MPC (Multi-Party Computation)
MPC allows multiple participants to jointly perform a computation without revealing their private inputs. MPC provides strong security guarantees but incurs high computational costs and suffers from a collusion problem.
Deco
In 2019, Deco first proposed an MPC-based TLS solution. Deco's maliciously secure two-party computation (2PC) approach has extensive compute overhead; for example, authenticating a 2KB data packet requires 475MB of communication and takes 50 seconds to complete. The solution is highly susceptible to timing out and has not been successfully deployed. Subsequently, Deco was acquired by Chainlink, who, along with Teller, developed a proof-of-concept solution.
TLSNotary
TLSNotary built upon Deco's work, utilizing a 2PC implementation based on garbled circuits and oblivious transfers. Garbled circuits are the simplest and most direct method in MPC.

TLS Notary "notarizes" the session between the client and server to prove its authenticity. During the TLS handshake, the prover and verifier collaborate to perform key encryption and decryption. Throughout the process, only the prover communicates with the server, while the verifier only sees encrypted data. The prover cannot forge inputs or responses. In the final stage, the prover can partially obscure the session record before presenting it to the verifier, for example, only proving to the verifier that it is located in a specific jurisdiction while concealing specific latitude and longitude information.
A validator can act as a notary, or outsource the validation role to generate more generic, portable proofs. This introduces an additional trust assumption that the validator must trust the notary not to collude with the prover to produce fake proofs. To mitigate this issue, a validator can request proofs from multiple notaries or define their own trusted notary list. However, these schemes still have various flaws, and the collusion problem remains one of the main challenges of MPC.
The advantage of TLSNotary is that it can maintain data portability, protect privacy, and does not rely on server cooperation. It achieves selectively disclosed authenticated data through circuit obfuscation and key splitting techniques but does not use ZKP. Currently, several projects have introduced zero-knowledge technology based on TLSNotary to make it easier to integrate.
Related Projects
Pluto
Pluto Labs is an open-source zero-knowledge TLSNotary implementation aimed at productizing it, allowing developers to integrate any off-chain data into smart contracts with just five lines of code. A detailed overview of its trust assumptions can be found in the related links.
Primus Labs (formerly PADO Labs)
Primus Labs has enhanced Deco using a garble-then-prove technique, replacing the high-cost malicious secure 2PC. It has achieved a 14x improvement in communication efficiency and up to a 15.5x improvement in execution time, successfully integrated into real-world APIs such as Coinbase and Twitter. Additionally, Primus is developing a zkFHE solution that may support more complex architectures in the future. Primus has also released a browser extension and plans to launch iOS/Android apps.
Opacity
Opacity addresses the collusion problem through a set of mechanisms and employs Eigenlayer AVS to provide economic security, overlaying multiple security measures:
· Sybil resistance based on on-chain Web2 account IDs
· Commit-and-reveal mechanism—users must submit a value before a randomly selected notary node
· Random selection of MPC nodes
· Verifiable attempt logs
Opacity restricts users from colluding using multiple wallets, with each wallet tied to a Web2 account. Additionally, users must submit a proof request before being randomly matched with a notary node, preventing them from changing their position if they attempt collusion without being matched to a colluding node. The verifiable attempt logs can be used to track suspicious proof submissions where a wallet attempts but fails to prove ownership of, for example, $10 million in bank deposits.
In addition, Opacity requires the attestation software to run in a Trusted Execution Environment (TEE) to ensure that unless the TEE is compromised, collusion is not possible. This is crucial because Opacity does not rely entirely on the TEE as a security guarantee.
To forge a proof within the Opacity framework, all of the following conditions must be met:
· User intentionally colludes
· At least one attestation node participates in collusion
· The attestation node runs on a compromised TEE
· The user randomly matches a collusion node within 1-3 attempts
· Verifiers can request proof regeneration multiple times, exponentially reducing the probability of the fourth condition
· Additionally, malicious behavior will face a penalty mechanism
The resistance to Sybil attacks in Opacity remains the weakest link. It can prevent one Web2 account from binding to multiple wallets but cannot prevent one person from creating multiple Web2 accounts. In fact, Opacity effectively outsources Sybil attack protection to Web2 platforms, with some platforms being more reliable than others (e.g., Rippling HR's identity authentication is more trustworthy than a Twitter account). In the future, Opacity may integrate multiple Web2 accounts to enhance security.
Opacity is developing the best practices implementation of zkTLS, making significant progress in decentralization and reducing trust assumptions. Its ability to overcome MPC computation overhead will be a key factor in future success.
In the future, there is still ample room for MPC performance optimization. For example, Vector Oblivious Linear Evaluation can achieve efficient 1-of-N Oblivious Transfer, leading to significant progress in each interaction. This can reduce network overhead by 100 times, making MPC-TLS proofs within 1 second feasible.
Proxy
An HTTPS proxy is an intermediary between a client and a server, responsible for forwarding encrypted traffic and only decrypting data when verifying user identity. Proxies can enhance security, performance, and privacy, particularly common in enterprise environments for monitoring and restricting employee access.

Proxies can also be used for zkTLS. This model inserts a proxy witness between the client and server to prove the legitimacy of communication. The proxy model is fast, cost-effective, and simple in structure, capable of handling large amounts of data. However, issues such as auditing, collusion, and decentralization persist. Additionally, this method can be detected by servers, potentially leading to blocking in widespread applications.
Reclaim Protocol
The Reclaim Protocol is the pioneer of the proxy model, leading the way in all zkTLS projects. Reclaim has broad support across almost all blockchains and boasts 889 community-built oracles. Several projects are built on Reclaim, including the zkP2P ticketing marketplace.
Reclaim is able to generate proofs on a user's mobile device in approximately 2–4 seconds without requiring users to download any apps or extensions. Reclaim employs a residential proxy to circumvent Web2 firewall issues.
Compared to MPC-TLS, Reclaim's proxy model is simpler, resulting in faster speeds. Many concerns about the proxy model have been addressed in the academic paper "Proxying is Enough" and Reclaim's blog. Studies show that the probability of breaking Reclaim's security is 10⁻⁴⁰.
zkPass
zkPass utilizes a hybrid model, originally based on an MPC approach but later transitioning to a proxy-witness model in production while keeping MPC as a fallback. zkPass is currently deployed on networks such as Base, BNB, Scroll, Linea, Arbitrum, zkSync, OP, X Layer, among others. zkPass uses its native TransGate Chrome extension and supports over 70 data sources and 200 data formats.
zkPass focuses primarily on identity verification and protection against Sybil attacks. The project is currently running incentive programs where users can complete challenges to earn ZKP token points. zkPass may become the first zkTLS project to introduce a liquidity token.
TEE
Trusted Execution Environment (TEE) is a tamper-resistant enclave in a processor that can store sensitive data and perform secure computations. TEE provides both hardware and software isolation, with dedicated memory and computational capabilities independent of the rest of the CPU. Intel SGX is currently the most well-known TEE solution. However, TEE has had vulnerabilities in the past and is susceptible to side-channel attacks.
Clique
Clique adopts a TEE-based approach to build zkTLS. This method offers very low computation and network overhead, addressing many issues but introducing a reliance on trusted hardware, shifting risks from notaries to chip manufacturers. In this model, TEE fully takes on the security guarantee responsibilities.
Summary
It is worth noting that zkTLS is just a generic term. Different zkTLS schemes vary in the degree of application of zero-knowledge technology and do not provide the same level of security guarantees as other zero-knowledge technologies like zkEmail. Strictly speaking, zkTLS may be better classified under MPC-TLS (+zkp), TEE-TLS, and zkTLS Proxy.
In the future, discussions in the zkTLS field will revolve around the trade-off between performance and security.

Proxy: This is a more general solution but requires additional trust assumptions, demands that clients can afford a zero-knowledge (ZK) solution, and also requires additional measures to bypass firewalls.
Multi-Party Computation (MPC): This model provides strong security guarantees but entails significant network communication overhead during MPC setup. Due to the high cost of the truth table, MPC methods are more suitable for small request/response interactions and TLS sessions without strict time limits. MPC has anti-censorship properties but faces collusion issues.
Trusted Execution Environment (TEE): The TEE model cleverly addresses most of the issues zkTLS faces, but at the cost of requiring full trust in TEE hardware.
Currently, Reclaim and Opacity are rapidly gaining momentum and seem to be leading the discussions in the zkTLS field. As zkTLS evolves, the trade-off between MPC and proxy models in terms of performance and security will remain a core topic.
Conclusion
zkTLS is an emerging narrative that is changing everything. However, many unresolved issues remain: Will zkTLS providers be commodified? Will the value capture flow to the application layer? How significant is the extractable value of forged proofs? How will these issues impact the discussions on zkTLS scheme trade-offs?
One thing is clear: zkTLS has greatly expanded the design space of decentralized applications and provided new ideas for building new systems. Today, many innovative ideas are already being implemented:
· Ticketing Marketplace – zkP2P (based on Reclaim)
· Web2 Reputation Import (Uber, DoorDash authentication) – Nosh Delivery (based on Opacity)
·KOL Marketing/Promotion Proof – Daisy (based on Opacity)
·Smart Predictions Market – TMR.NEWS (based on Reclaim)
·Low Collateral Loans through Payroll Earn – Earnifi (based on Opacity)
·Precision Targeting with Digital Ad Incentives – EarnOS (based on Opacity)
·Soft Collateral Loans – 3Jane (based on Reclaim)
zkTLS has disrupted the existing market landscape of Web2 by weakening data monopolies. All current inefficient markets are opportunities for cryptographic technology to penetrate and improve society.
You may also like

Token Cannot Compound, Where Is the Real Investment Opportunity?

February 6th Market Key Intelligence, How Much Did You Miss?

China's Central Bank and Eight Other Departments' Latest Regulatory Focus: Key Attention to RWA Tokenized Asset Risk
Foreword: Today, the People's Bank of China's website published the "Notice of the People's Bank of China, National Development and Reform Commission, Ministry of Industry and Information Technology, Ministry of Public Security, State Administration for Market Regulation, China Banking and Insurance Regulatory Commission, China Securities Regulatory Commission, State Administration of Foreign Exchange on Further Preventing and Dealing with Risks Related to Virtual Currency and Others (Yinfa [2026] No. 42)", the latest regulatory requirements from the eight departments including the central bank, which are basically consistent with the regulatory requirements of recent years. The main focus of the regulation is on speculative activities such as virtual currency trading, exchanges, ICOs, overseas platform services, and this time, regulatory oversight of RWA has been added, explicitly prohibiting RWA tokenization, stablecoins (especially those pegged to the RMB). The following is the full text:
To the people's governments of all provinces, autonomous regions, and municipalities directly under the Central Government, the Xinjiang Production and Construction Corps:
Recently, there have been speculative activities related to virtual currency and Real-World Assets (RWA) tokenization, disrupting the economic and financial order and jeopardizing the property security of the people. In order to further prevent and address the risks related to virtual currency and Real-World Assets tokenization, effectively safeguard national security and social stability, in accordance with the "Law of the People's Republic of China on the People's Bank of China," "Law of the People's Republic of China on Commercial Banks," "Securities Law of the People's Republic of China," "Law of the People's Republic of China on Securities Investment Funds," "Law of the People's Republic of China on Futures and Derivatives," "Cybersecurity Law of the People's Republic of China," "Regulations of the People's Republic of China on the Administration of Renminbi," "Regulations on Prevention and Disposal of Illegal Fundraising," "Regulations of the People's Republic of China on Foreign Exchange Administration," "Telecommunications Regulations of the People's Republic of China," and other provisions, after reaching consensus with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, and with the approval of the State Council, the relevant matters are notified as follows:
(I) Virtual currency does not possess the legal status equivalent to fiat currency. Virtual currencies such as Bitcoin, Ether, Tether, etc., have the main characteristics of being issued by non-monetary authorities, using encryption technology and distributed ledger or similar technology, existing in digital form, etc. They do not have legal tender status, should not and cannot be circulated and used as currency in the market.
The business activities related to virtual currency are classified as illegal financial activities. The exchange of fiat currency and virtual currency within the territory, exchange of virtual currencies, acting as a central counterparty in buying and selling virtual currencies, providing information intermediary and pricing services for virtual currency transactions, token issuance financing, and trading of virtual currency-related financial products, etc., fall under illegal financial activities, such as suspected illegal issuance of token vouchers, unauthorized public issuance of securities, illegal operation of securities and futures business, illegal fundraising, etc., are strictly prohibited across the board and resolutely banned in accordance with the law. Overseas entities and individuals are not allowed to provide virtual currency-related services to domestic entities in any form.
A stablecoin pegged to a fiat currency indirectly fulfills some functions of the fiat currency in circulation. Without the consent of relevant authorities in accordance with the law and regulations, any domestic or foreign entity or individual is not allowed to issue a RMB-pegged stablecoin overseas.
(II)Tokenization of Real-World Assets refers to the use of encryption technology and distributed ledger or similar technologies to transform ownership rights, income rights, etc., of assets into tokens (tokens) or other interests or bond certificates with token (token) characteristics, and carry out issuance and trading activities.
Engaging in the tokenization of real-world assets domestically, as well as providing related intermediary, information technology services, etc., which are suspected of illegal issuance of token vouchers, unauthorized public offering of securities, illegal operation of securities and futures business, illegal fundraising, and other illegal financial activities, shall be prohibited; except for relevant business activities carried out with the approval of the competent authorities in accordance with the law and regulations and relying on specific financial infrastructures. Overseas entities and individuals are not allowed to illegally provide services related to the tokenization of real-world assets to domestic entities in any form.
(III) Inter-agency Coordination. The People's Bank of China, together with the National Development and Reform Commission, the Ministry of Industry and Information Technology, the Ministry of Public Security, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the China Securities Regulatory Commission, the State Administration of Foreign Exchange, and other departments, will improve the work mechanism, strengthen coordination with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, coordinate efforts, and overall guide regions to carry out risk prevention and disposal of virtual currency-related illegal financial activities.
The China Securities Regulatory Commission, together with the National Development and Reform Commission, the Ministry of Industry and Information Technology, the Ministry of Public Security, the People's Bank of China, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the State Administration of Foreign Exchange, and other departments, will improve the work mechanism, strengthen coordination with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, coordinate efforts, and overall guide regions to carry out risk prevention and disposal of illegal financial activities related to the tokenization of real-world assets.
(IV) Strengthening Local Implementation. The people's governments at the provincial level are overall responsible for the prevention and disposal of risks related to virtual currencies and the tokenization of real-world assets in their respective administrative regions. The specific leading department is the local financial regulatory department, with participation from branches and dispatched institutions of the State Council's financial regulatory department, telecommunications regulators, public security, market supervision, and other departments, in coordination with cyberspace departments, courts, and procuratorates, to improve the normalization of the work mechanism, effectively connect with the relevant work mechanisms of central departments, form a cooperative and coordinated working pattern between central and local governments, effectively prevent and properly handle risks related to virtual currencies and the tokenization of real-world assets, and maintain economic and financial order and social stability.
(5) Enhanced Risk Monitoring. The People's Bank of China, China Securities Regulatory Commission, National Development and Reform Commission, Ministry of Industry and Information Technology, Ministry of Public Security, State Administration of Foreign Exchange, Cyberspace Administration of China, and other departments continue to improve monitoring techniques and system support, enhance cross-departmental data analysis and sharing, establish sound information sharing and cross-validation mechanisms, promptly grasp the risk situation of activities related to virtual currency and real-world asset tokenization. Local governments at all levels give full play to the role of local monitoring and early warning mechanisms. Local financial regulatory authorities, together with branches and agencies of the State Council's financial regulatory authorities, as well as departments of cyberspace and public security, ensure effective connection between online monitoring, offline investigation, and fund tracking, efficiently and accurately identify activities related to virtual currency and real-world asset tokenization, promptly share risk information, improve early warning information dissemination, verification, and rapid response mechanisms.
(6) Strengthened Oversight of Financial Institutions, Intermediaries, and Technology Service Providers. Financial institutions (including non-bank payment institutions) are prohibited from providing account opening, fund transfer, and clearing services for virtual currency-related business activities, issuing and selling financial products related to virtual currency, including virtual currency and related financial products in the scope of collateral, conducting insurance business related to virtual currency, or including virtual currency in the scope of insurance liability. Financial institutions (including non-bank payment institutions) are prohibited from providing custody, clearing, and settlement services for unauthorized real-world asset tokenization-related business and related financial products. Relevant intermediary institutions and information technology service providers are prohibited from providing intermediary, technical, or other services for unauthorized real-world asset tokenization-related businesses and related financial products.
(7) Enhanced Management of Internet Information Content and Access. Internet enterprises are prohibited from providing online business venues, commercial displays, marketing, advertising, or paid traffic diversion services for virtual currency and real-world asset tokenization-related business activities. Upon discovering clues of illegal activities, they should promptly report to relevant departments and provide technical support and assistance for related investigations and inquiries. Based on the clues transferred by the financial regulatory authorities, the cyberspace administration, telecommunications authorities, and public security departments should promptly close and deal with websites, mobile applications (including mini-programs), and public accounts engaged in virtual currency and real-world asset tokenization-related business activities in accordance with the law.
(8) Strengthened Entity Registration and Advertisement Management. Market supervision departments strengthen entity registration and management, and enterprise and individual business registrations must not contain terms such as "virtual currency," "virtual asset," "cryptocurrency," "crypto asset," "stablecoin," "real-world asset tokenization," or "RWA" in their names or business scopes. Market supervision departments, together with financial regulatory authorities, legally enhance the supervision of advertisements related to virtual currency and real-world asset tokenization, promptly investigating and handling relevant illegal advertisements.
(IX) Continued Rectification of Virtual Currency Mining Activities. The National Development and Reform Commission, together with relevant departments, strictly controls virtual currency mining activities, continuously promotes the rectification of virtual currency mining activities. The people's governments of various provinces take overall responsibility for the rectification of "mining" within their respective administrative regions. In accordance with the requirements of the National Development and Reform Commission and other departments in the "Notice on the Rectification of Virtual Currency Mining Activities" (NDRC Energy-saving Building [2021] No. 1283) and the provisions of the "Guidance Catalog for Industrial Structure Adjustment (2024 Edition)," a comprehensive review, investigation, and closure of existing virtual currency mining projects are conducted, new mining projects are strictly prohibited, and mining machine production enterprises are strictly prohibited from providing mining machine sales and other services within the country.
(X) Severe Crackdown on Related Illegal Financial Activities. Upon discovering clues to illegal financial activities related to virtual currency and the tokenization of real-world assets, local financial regulatory authorities, branches of the State Council's financial regulatory authorities, and other relevant departments promptly investigate, determine, and properly handle the issues in accordance with the law, and seriously hold the relevant entities and individuals legally responsible. Those suspected of crimes are transferred to the judicial authorities for processing according to the law.
(XI) Severe Crackdown on Related Illegal and Criminal Activities. The Ministry of Public Security, the People's Bank of China, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the China Securities Regulatory Commission, as well as judicial and procuratorial organs, in accordance with their respective responsibilities, rigorously crack down on illegal and criminal activities related to virtual currency, the tokenization of real-world assets, such as fraud, money laundering, illegal business operations, pyramid schemes, illegal fundraising, and other illegal and criminal activities carried out under the guise of virtual currency, the tokenization of real-world assets, etc.
(XII) Strengthen Industry Self-discipline. Relevant industry associations should enhance membership management and policy advocacy, based on their own responsibilities, advocate and urge member units to resist illegal financial activities related to virtual currency and the tokenization of real-world assets. Member units that violate regulatory policies and industry self-discipline rules are to be disciplined in accordance with relevant self-regulatory management regulations. By leveraging various industry infrastructure, conduct risk monitoring related to virtual currency, the tokenization of real-world assets, and promptly transfer issue clues to relevant departments.
(XIII) Without the approval of relevant departments in accordance with the law and regulations, domestic entities and foreign entities controlled by them may not issue virtual currency overseas.
(XIV) Domestic entities engaging directly or indirectly in overseas external debt-based tokenization of real-world assets, or conducting asset securitization activities abroad based on domestic ownership rights, income rights, etc. (hereinafter referred to as domestic equity), should be strictly regulated in accordance with the principles of "same business, same risk, same rules." The National Development and Reform Commission, the China Securities Regulatory Commission, the State Administration of Foreign Exchange, and other relevant departments regulate it according to their respective responsibilities. For other forms of overseas real-world asset tokenization activities based on domestic equity by domestic entities, the China Securities Regulatory Commission, together with relevant departments, supervise according to their division of responsibilities. Without the consent and filing of relevant departments, no unit or individual may engage in the above-mentioned business.
(15) Overseas subsidiaries and branches of domestic financial institutions providing Real World Asset Tokenization-related services overseas shall do so legally and prudently. They shall have professional personnel and systems in place to effectively mitigate business risks, strictly implement customer onboarding, suitability management, anti-money laundering requirements, and incorporate them into the domestic financial institutions' compliance and risk management system. Intermediaries and information technology service providers offering Real World Asset Tokenization services abroad based on domestic equity or conducting Real World Asset Tokenization business in the form of overseas debt for domestic entities directly or indirectly venturing abroad must strictly comply with relevant laws and regulations. They should establish and improve relevant compliance and internal control systems in accordance with relevant normative requirements, strengthen business and risk control, and report the business developments to the relevant regulatory authorities for approval or filing.
(16) Strengthen organizational leadership and overall coordination. All departments and regions should attach great importance to the prevention of risks related to virtual currencies and Real World Asset Tokenization, strengthen organizational leadership, clarify work responsibilities, form a long-term effective working mechanism with centralized coordination, local implementation, and shared responsibilities, maintain high pressure, dynamically monitor risks, effectively prevent and mitigate risks in an orderly and efficient manner, legally protect the property security of the people, and make every effort to maintain economic and financial order and social stability.
(17) Widely carry out publicity and education. All departments, regions, and industry associations should make full use of various media and other communication channels to disseminate information through legal and policy interpretation, analysis of typical cases, and education on investment risks, etc. They should promote the illegality and harm of virtual currencies and Real World Asset Tokenization-related businesses and their manifestations, fully alert to potential risks and hidden dangers, and enhance public awareness and identification capabilities for risk prevention.
(18) Engaging in illegal financial activities related to virtual currencies and Real World Asset Tokenization in violation of this notice, as well as providing services for virtual currencies and Real World Asset Tokenization-related businesses, shall be punished in accordance with relevant regulations. If it constitutes a crime, criminal liability shall be pursued according to the law. For domestic entities and individuals who knowingly or should have known that overseas entities illegally provided virtual currency or Real World Asset Tokenization-related services to domestic entities and still assisted them, relevant responsibilities shall be pursued according to the law. If it constitutes a crime, criminal liability shall be pursued according to the law.
(19) If any unit or individual invests in virtual currencies, Real World Asset Tokens, and related financial products against public order and good customs, the relevant civil legal actions shall be invalid, and any resulting losses shall be borne by them. If there are suspicions of disrupting financial order and jeopardizing financial security, the relevant departments shall deal with them according to the law.
This notice shall enter into force upon the date of its issuance. The People's Bank of China and ten other departments' "Notice on Further Preventing and Dealing with the Risks of Virtual Currency Trading Speculation" (Yinfa [2021] No. 237) is hereby repealed.

Former Partner's Perspective on Multicoin: Kyle's Exit, But the Game He Left Behind Just Getting Started

Why Bitcoin Is Falling Now: The Real Reasons Behind BTC's Crash & WEEX's Smart Profit Playbook
Bitcoin's ongoing crash explained: Discover the 5 hidden triggers behind BTC's plunge & how WEEX's Auto Earn and Trade to Earn strategies help traders profit from crypto market volatility.

Wall Street's Hottest Trades See Exodus

Vitalik Discusses Ethereum Scaling Path, Circle Announces Partnership with Polymarket, What's the Overseas Crypto Community Talking About Today?

Believing in the Capital Markets - The Essence and Core Value of Cryptocurrency

Polymarket's 'Weatherman': Predict Temperature, Win Million-Dollar Payout

$15K+ Profits: The 4 AI Trading Secrets WEEX Hackathon Prelim Winners Used to Dominate Volatile Crypto Markets
How WEEX Hackathon's top AI trading strategies made $15K+ in crypto markets: 4 proven rules for ETH/BTC trading, market structure analysis, and risk management in volatile conditions.

A nearly 20% one-day plunge, how long has it been since you last saw a $60,000 Bitcoin?

Raoul Pal: I've seen every single panic, and they are never the end.

Key Market Information Discrepancy on February 6th - A Must-Read! | Alpha Morning Report

2026 Crypto Industry's First Snowfall

The Harsh Reality Behind the $26 Billion Crypto Liquidation: Liquidity Is Killing the Market

Why Is Gold, US Stocks, Bitcoin All Falling?

Key Market Intelligence for February 5th, how much did you miss out on?

Wintermute: By 2026, crypto had gradually become the settlement layer of the Internet economy
Token Cannot Compound, Where Is the Real Investment Opportunity?
February 6th Market Key Intelligence, How Much Did You Miss?
China's Central Bank and Eight Other Departments' Latest Regulatory Focus: Key Attention to RWA Tokenized Asset Risk
Foreword: Today, the People's Bank of China's website published the "Notice of the People's Bank of China, National Development and Reform Commission, Ministry of Industry and Information Technology, Ministry of Public Security, State Administration for Market Regulation, China Banking and Insurance Regulatory Commission, China Securities Regulatory Commission, State Administration of Foreign Exchange on Further Preventing and Dealing with Risks Related to Virtual Currency and Others (Yinfa [2026] No. 42)", the latest regulatory requirements from the eight departments including the central bank, which are basically consistent with the regulatory requirements of recent years. The main focus of the regulation is on speculative activities such as virtual currency trading, exchanges, ICOs, overseas platform services, and this time, regulatory oversight of RWA has been added, explicitly prohibiting RWA tokenization, stablecoins (especially those pegged to the RMB). The following is the full text:
To the people's governments of all provinces, autonomous regions, and municipalities directly under the Central Government, the Xinjiang Production and Construction Corps:
Recently, there have been speculative activities related to virtual currency and Real-World Assets (RWA) tokenization, disrupting the economic and financial order and jeopardizing the property security of the people. In order to further prevent and address the risks related to virtual currency and Real-World Assets tokenization, effectively safeguard national security and social stability, in accordance with the "Law of the People's Republic of China on the People's Bank of China," "Law of the People's Republic of China on Commercial Banks," "Securities Law of the People's Republic of China," "Law of the People's Republic of China on Securities Investment Funds," "Law of the People's Republic of China on Futures and Derivatives," "Cybersecurity Law of the People's Republic of China," "Regulations of the People's Republic of China on the Administration of Renminbi," "Regulations on Prevention and Disposal of Illegal Fundraising," "Regulations of the People's Republic of China on Foreign Exchange Administration," "Telecommunications Regulations of the People's Republic of China," and other provisions, after reaching consensus with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, and with the approval of the State Council, the relevant matters are notified as follows:
(I) Virtual currency does not possess the legal status equivalent to fiat currency. Virtual currencies such as Bitcoin, Ether, Tether, etc., have the main characteristics of being issued by non-monetary authorities, using encryption technology and distributed ledger or similar technology, existing in digital form, etc. They do not have legal tender status, should not and cannot be circulated and used as currency in the market.
The business activities related to virtual currency are classified as illegal financial activities. The exchange of fiat currency and virtual currency within the territory, exchange of virtual currencies, acting as a central counterparty in buying and selling virtual currencies, providing information intermediary and pricing services for virtual currency transactions, token issuance financing, and trading of virtual currency-related financial products, etc., fall under illegal financial activities, such as suspected illegal issuance of token vouchers, unauthorized public issuance of securities, illegal operation of securities and futures business, illegal fundraising, etc., are strictly prohibited across the board and resolutely banned in accordance with the law. Overseas entities and individuals are not allowed to provide virtual currency-related services to domestic entities in any form.
A stablecoin pegged to a fiat currency indirectly fulfills some functions of the fiat currency in circulation. Without the consent of relevant authorities in accordance with the law and regulations, any domestic or foreign entity or individual is not allowed to issue a RMB-pegged stablecoin overseas.
(II)Tokenization of Real-World Assets refers to the use of encryption technology and distributed ledger or similar technologies to transform ownership rights, income rights, etc., of assets into tokens (tokens) or other interests or bond certificates with token (token) characteristics, and carry out issuance and trading activities.
Engaging in the tokenization of real-world assets domestically, as well as providing related intermediary, information technology services, etc., which are suspected of illegal issuance of token vouchers, unauthorized public offering of securities, illegal operation of securities and futures business, illegal fundraising, and other illegal financial activities, shall be prohibited; except for relevant business activities carried out with the approval of the competent authorities in accordance with the law and regulations and relying on specific financial infrastructures. Overseas entities and individuals are not allowed to illegally provide services related to the tokenization of real-world assets to domestic entities in any form.
(III) Inter-agency Coordination. The People's Bank of China, together with the National Development and Reform Commission, the Ministry of Industry and Information Technology, the Ministry of Public Security, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the China Securities Regulatory Commission, the State Administration of Foreign Exchange, and other departments, will improve the work mechanism, strengthen coordination with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, coordinate efforts, and overall guide regions to carry out risk prevention and disposal of virtual currency-related illegal financial activities.
The China Securities Regulatory Commission, together with the National Development and Reform Commission, the Ministry of Industry and Information Technology, the Ministry of Public Security, the People's Bank of China, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the State Administration of Foreign Exchange, and other departments, will improve the work mechanism, strengthen coordination with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, coordinate efforts, and overall guide regions to carry out risk prevention and disposal of illegal financial activities related to the tokenization of real-world assets.
(IV) Strengthening Local Implementation. The people's governments at the provincial level are overall responsible for the prevention and disposal of risks related to virtual currencies and the tokenization of real-world assets in their respective administrative regions. The specific leading department is the local financial regulatory department, with participation from branches and dispatched institutions of the State Council's financial regulatory department, telecommunications regulators, public security, market supervision, and other departments, in coordination with cyberspace departments, courts, and procuratorates, to improve the normalization of the work mechanism, effectively connect with the relevant work mechanisms of central departments, form a cooperative and coordinated working pattern between central and local governments, effectively prevent and properly handle risks related to virtual currencies and the tokenization of real-world assets, and maintain economic and financial order and social stability.
(5) Enhanced Risk Monitoring. The People's Bank of China, China Securities Regulatory Commission, National Development and Reform Commission, Ministry of Industry and Information Technology, Ministry of Public Security, State Administration of Foreign Exchange, Cyberspace Administration of China, and other departments continue to improve monitoring techniques and system support, enhance cross-departmental data analysis and sharing, establish sound information sharing and cross-validation mechanisms, promptly grasp the risk situation of activities related to virtual currency and real-world asset tokenization. Local governments at all levels give full play to the role of local monitoring and early warning mechanisms. Local financial regulatory authorities, together with branches and agencies of the State Council's financial regulatory authorities, as well as departments of cyberspace and public security, ensure effective connection between online monitoring, offline investigation, and fund tracking, efficiently and accurately identify activities related to virtual currency and real-world asset tokenization, promptly share risk information, improve early warning information dissemination, verification, and rapid response mechanisms.
(6) Strengthened Oversight of Financial Institutions, Intermediaries, and Technology Service Providers. Financial institutions (including non-bank payment institutions) are prohibited from providing account opening, fund transfer, and clearing services for virtual currency-related business activities, issuing and selling financial products related to virtual currency, including virtual currency and related financial products in the scope of collateral, conducting insurance business related to virtual currency, or including virtual currency in the scope of insurance liability. Financial institutions (including non-bank payment institutions) are prohibited from providing custody, clearing, and settlement services for unauthorized real-world asset tokenization-related business and related financial products. Relevant intermediary institutions and information technology service providers are prohibited from providing intermediary, technical, or other services for unauthorized real-world asset tokenization-related businesses and related financial products.
(7) Enhanced Management of Internet Information Content and Access. Internet enterprises are prohibited from providing online business venues, commercial displays, marketing, advertising, or paid traffic diversion services for virtual currency and real-world asset tokenization-related business activities. Upon discovering clues of illegal activities, they should promptly report to relevant departments and provide technical support and assistance for related investigations and inquiries. Based on the clues transferred by the financial regulatory authorities, the cyberspace administration, telecommunications authorities, and public security departments should promptly close and deal with websites, mobile applications (including mini-programs), and public accounts engaged in virtual currency and real-world asset tokenization-related business activities in accordance with the law.
(8) Strengthened Entity Registration and Advertisement Management. Market supervision departments strengthen entity registration and management, and enterprise and individual business registrations must not contain terms such as "virtual currency," "virtual asset," "cryptocurrency," "crypto asset," "stablecoin," "real-world asset tokenization," or "RWA" in their names or business scopes. Market supervision departments, together with financial regulatory authorities, legally enhance the supervision of advertisements related to virtual currency and real-world asset tokenization, promptly investigating and handling relevant illegal advertisements.
(IX) Continued Rectification of Virtual Currency Mining Activities. The National Development and Reform Commission, together with relevant departments, strictly controls virtual currency mining activities, continuously promotes the rectification of virtual currency mining activities. The people's governments of various provinces take overall responsibility for the rectification of "mining" within their respective administrative regions. In accordance with the requirements of the National Development and Reform Commission and other departments in the "Notice on the Rectification of Virtual Currency Mining Activities" (NDRC Energy-saving Building [2021] No. 1283) and the provisions of the "Guidance Catalog for Industrial Structure Adjustment (2024 Edition)," a comprehensive review, investigation, and closure of existing virtual currency mining projects are conducted, new mining projects are strictly prohibited, and mining machine production enterprises are strictly prohibited from providing mining machine sales and other services within the country.
(X) Severe Crackdown on Related Illegal Financial Activities. Upon discovering clues to illegal financial activities related to virtual currency and the tokenization of real-world assets, local financial regulatory authorities, branches of the State Council's financial regulatory authorities, and other relevant departments promptly investigate, determine, and properly handle the issues in accordance with the law, and seriously hold the relevant entities and individuals legally responsible. Those suspected of crimes are transferred to the judicial authorities for processing according to the law.
(XI) Severe Crackdown on Related Illegal and Criminal Activities. The Ministry of Public Security, the People's Bank of China, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the China Securities Regulatory Commission, as well as judicial and procuratorial organs, in accordance with their respective responsibilities, rigorously crack down on illegal and criminal activities related to virtual currency, the tokenization of real-world assets, such as fraud, money laundering, illegal business operations, pyramid schemes, illegal fundraising, and other illegal and criminal activities carried out under the guise of virtual currency, the tokenization of real-world assets, etc.
(XII) Strengthen Industry Self-discipline. Relevant industry associations should enhance membership management and policy advocacy, based on their own responsibilities, advocate and urge member units to resist illegal financial activities related to virtual currency and the tokenization of real-world assets. Member units that violate regulatory policies and industry self-discipline rules are to be disciplined in accordance with relevant self-regulatory management regulations. By leveraging various industry infrastructure, conduct risk monitoring related to virtual currency, the tokenization of real-world assets, and promptly transfer issue clues to relevant departments.
(XIII) Without the approval of relevant departments in accordance with the law and regulations, domestic entities and foreign entities controlled by them may not issue virtual currency overseas.
(XIV) Domestic entities engaging directly or indirectly in overseas external debt-based tokenization of real-world assets, or conducting asset securitization activities abroad based on domestic ownership rights, income rights, etc. (hereinafter referred to as domestic equity), should be strictly regulated in accordance with the principles of "same business, same risk, same rules." The National Development and Reform Commission, the China Securities Regulatory Commission, the State Administration of Foreign Exchange, and other relevant departments regulate it according to their respective responsibilities. For other forms of overseas real-world asset tokenization activities based on domestic equity by domestic entities, the China Securities Regulatory Commission, together with relevant departments, supervise according to their division of responsibilities. Without the consent and filing of relevant departments, no unit or individual may engage in the above-mentioned business.
(15) Overseas subsidiaries and branches of domestic financial institutions providing Real World Asset Tokenization-related services overseas shall do so legally and prudently. They shall have professional personnel and systems in place to effectively mitigate business risks, strictly implement customer onboarding, suitability management, anti-money laundering requirements, and incorporate them into the domestic financial institutions' compliance and risk management system. Intermediaries and information technology service providers offering Real World Asset Tokenization services abroad based on domestic equity or conducting Real World Asset Tokenization business in the form of overseas debt for domestic entities directly or indirectly venturing abroad must strictly comply with relevant laws and regulations. They should establish and improve relevant compliance and internal control systems in accordance with relevant normative requirements, strengthen business and risk control, and report the business developments to the relevant regulatory authorities for approval or filing.
(16) Strengthen organizational leadership and overall coordination. All departments and regions should attach great importance to the prevention of risks related to virtual currencies and Real World Asset Tokenization, strengthen organizational leadership, clarify work responsibilities, form a long-term effective working mechanism with centralized coordination, local implementation, and shared responsibilities, maintain high pressure, dynamically monitor risks, effectively prevent and mitigate risks in an orderly and efficient manner, legally protect the property security of the people, and make every effort to maintain economic and financial order and social stability.
(17) Widely carry out publicity and education. All departments, regions, and industry associations should make full use of various media and other communication channels to disseminate information through legal and policy interpretation, analysis of typical cases, and education on investment risks, etc. They should promote the illegality and harm of virtual currencies and Real World Asset Tokenization-related businesses and their manifestations, fully alert to potential risks and hidden dangers, and enhance public awareness and identification capabilities for risk prevention.
(18) Engaging in illegal financial activities related to virtual currencies and Real World Asset Tokenization in violation of this notice, as well as providing services for virtual currencies and Real World Asset Tokenization-related businesses, shall be punished in accordance with relevant regulations. If it constitutes a crime, criminal liability shall be pursued according to the law. For domestic entities and individuals who knowingly or should have known that overseas entities illegally provided virtual currency or Real World Asset Tokenization-related services to domestic entities and still assisted them, relevant responsibilities shall be pursued according to the law. If it constitutes a crime, criminal liability shall be pursued according to the law.
(19) If any unit or individual invests in virtual currencies, Real World Asset Tokens, and related financial products against public order and good customs, the relevant civil legal actions shall be invalid, and any resulting losses shall be borne by them. If there are suspicions of disrupting financial order and jeopardizing financial security, the relevant departments shall deal with them according to the law.
This notice shall enter into force upon the date of its issuance. The People's Bank of China and ten other departments' "Notice on Further Preventing and Dealing with the Risks of Virtual Currency Trading Speculation" (Yinfa [2021] No. 237) is hereby repealed.
Former Partner's Perspective on Multicoin: Kyle's Exit, But the Game He Left Behind Just Getting Started
Why Bitcoin Is Falling Now: The Real Reasons Behind BTC's Crash & WEEX's Smart Profit Playbook
Bitcoin's ongoing crash explained: Discover the 5 hidden triggers behind BTC's plunge & how WEEX's Auto Earn and Trade to Earn strategies help traders profit from crypto market volatility.

 Earn
Earn